Why Real-Time Data Protection Has Become Table Stakes for Security Leaders
Security
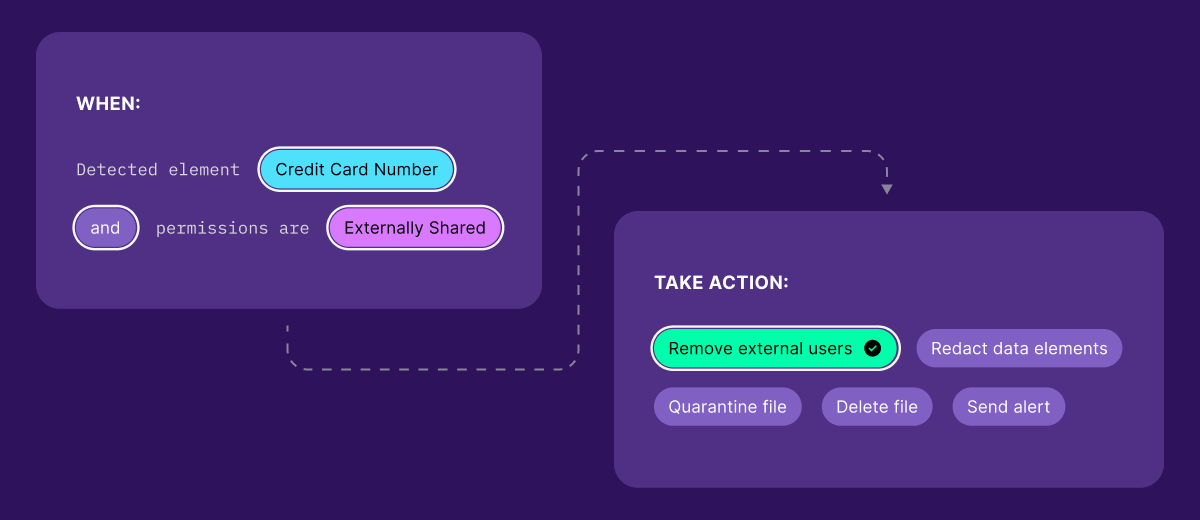
As modern data environments become increasingly complex and fragmented, security leaders — especially those in highly-regulated verticals — are facing increased pressure to shift toward more proactive data protection strategies.
This pressure isn’t without merit. In 2024 alone, there were over 4,100 publicly disclosed data breaches, most of which initially flew under the radar due to reliance on after-the-fact detection and remediation. With 2025 on track to match or exceed that number, it’s become evident that real-time protection of both at-rest and in-motion data is no longer optional but essential. So, how can your organization make the shift?
This article explores where reactive security posture management falls short, why real-time data protection has become table stakes for security leaders, and how leading organizations (like Ramp) use Teleskope to shift to proactive protection without friction.
Why Reactive Security Posture Management Falls Short
According to Horizon3’s State of Cybersecurity in 2025 Report, over 30% of organizations admit to having a reactive data protection strategy. This means they rely primarily on scheduled, periodic scanning, classification, and remediation of sensitive data at rest. The only time when they break this mold is when an attack has already occurred.
The problem with this approach is that it fails to keep pace with modern data environments. Globally, over 400,000 petabytes of sensitive information are generated every day, circulating between cloud data stores, SaaS tools, and on-prem systems. As data sprawl and fragmented visibility become the new norm, sensitive information is regularly left exposed between periodic scans (often for weeks to months), significantly increasing the risk of a costly data breach.
The shortcomings of reactive data protection don’t stop at visibility. Even when vulnerabilities are uncovered, security teams are often too encumbered to address each one promptly. Between alert fatigue from reactionary scans and an industry-wide shortage of resources, it takes the average security team over 65 days to remediate a single vulnerability. In some cases, vulnerabilities deemed less critical may not be remediated at all.
Simply put, reactive data protection transforms a security leader’s job into an unscalable half measure that leaves their organization at risk of direct financial losses, eroding reputation, and compromised customer trust. Fortunately, real-time data protection solutions (like Teleskope) are empowering security leaders to regain control over their sprawling data footprint.
“Real-time data protection gives security leaders the power to stop breaches before they happen. That’s the holy grail for CISOs under pressure to minimize risk while enabling digital transformation.” — Naveen Palavalli, VP of Product Strategy, Palo Alto Networks
How Real-Time Data Protection Addresses These Shortcomings
To enforce and maintain data protection at scale, security leaders must shift toward real-time scanning, classification, and remediation of at-rest and in-motion data. Bringing these capabilities into real-time not only empowers security leaders to take a prevention-based approach to data security, but also helps their organizations remain nimble across evolving data environments.
Here’s a quick look at some of the tangible benefits of real-time data protection:
Continuous Visibility and Data Classification
Shifting from reactive to real-time data protection empowers security leaders to instantly identify and classify sensitive information across their entire data footprint. Whether it be PII collected through web forms or secrets stored across on-prem systems, real-time data protection ensures all sensitive information is accounted for, rather than being left exposed between periodical scans.
Beyond comprehensive visibility and classification, real-time data protection enables security leaders to identify advanced patterns and anomalous behaviors that periodic scans frequently miss. From zero-day vulnerabilities to evolving malware variants that lack existing signatures, real-time data protection ensures even the most unusual edge cases are promptly identified.
End-to-end data protection tools like Teleskope can help security leaders achieve this level of visibility (while streamlining classification and remediation flows in tandem). With a comprehensive and real-time view of sensitive information (including PII, PHI, PCI, and secrets) living across cloud, on-premises, and third-party environments, Teleskope makes the transition from reactive to proactive data protection seamless.
Streamlined Remediation
While continuous visibility is the first step in a real-time data protection strategy, automated remediation is equally (if not more) significant.
According to recent research by Exabeam and IDC, 57% of organizations experience security gaps caused by overloaded teams lacking automated remediation resources. When security leaders equip their teams with these resources, they gain the ability to both identify risks and enforce data protection at scale.
Enabling immediate, predefined actions in response to detected risks also saves valuable time traditionally spent on manual remediation. Risks that might have taken hours or days of manual triage are easily remedied in minutes or even seconds. This rapid turnaround not only minimizes the window of vulnerability but also reduces the burden on security teams, who can redirect their attention to higher-value tasks instead of routine fixes.
Moreover, automated remediation scales effortlessly alongside organizational growth, ensuring consistent protection without requiring proportional increases in security personnel or resources. This scalability is essential as enterprises handle escalating volumes of data across increasingly complex environments.
While many DSPM tools offer automated visibility, they often lack native remediation capabilities, leaving security teams to address threats manually. Traditionally, remediation has been the domain of Data Loss Prevention (DLP) platforms. However, DLP tools are notoriously difficult to deploy and manage, struggle with accurate data classification, and typically only cover endpoint and SaaS environments, not internal data stores. They often require sweeping permissions and access, yet do nothing to provide visibility into where sensitive data lives and how it’s used. In short, DLP solutions have proven difficult to extract value from, and do little to illuminate the underlying data landscape.
For security leaders seeking true end-to-end data protection, Teleskope goes further, supporting custom policies that empower organizations to automatically remediate vulnerabilities at the source. This means security gaps aren’t just detected, but can be addressed without bottlenecks, offering end-to-end protection from visibility all the way through remediation.
Resource Efficiency and Time Savings
With real-time data protection, security leaders and their teams are no longer caught in a perpetual cycle of catch-up. Rather than security teams logging on and wading through a continuous stream of alerts and backlogged remediation tasks, they can automatically identify, categorize, and address risks as they arise. This approach not only eliminates alert fatigue, but also empowers security teams to reclaim bandwidth for strategic decision-making and forensic analysis on unique edge cases.
However, time and efficiency gains realized from shifting to real-time data protection are strongly linked to one’s security stack. If your organization relies on a patchwork of DSPM tools for visibility alone, the sheer amount of context switching your security teams will experience daily can quickly erode those gains. As such, security leaders should seek comprehensive solutions that address each step of their data protection workflow in one unified platform.
Building What Security Leaders Need: Our Vision at Teleskope
As a solution founded by former security leaders at Fortune 500 companies, Teleskope takes a different approach than most DSPM and DLP tools when it comes to real-time data protection.
Our team saw how daunting a modern security leader’s job can be. From monitoring sprawling data footprints to managing multiple tools (each with its own classification and policy enforcement standards), security leaders frequently operate in noisy and hectic environments that bog down their data protection efforts. Rather than contributing to this noise, Teleskope was created to be the only security solution you need, one that combines the visibility of a DPSM platform with the real-time remediation of a DLP product, all within a single, unified platform.
To bring this vision into reality, our team conducted exhaustive research into the core challenges security leaders face today, factoring their greatest pain points into the development of our solution. It started with visibility and classifications, the building blocks of any data protection strategy. Security leaders needed real-time visibility into both at-rest and in-motion data across their entire data footprint, combined with bespoke and automated classification flows that require minimal manual intervention. To address this need, our team built a multi-model machine learning pipeline to automatically detect and classify over 150 types of sensitive data — including PII, PHI, PCI, and secrets — across cloud, on-premises, and third-party environments.
We believe that visibility without real-time remediation is insufficient for modern data security — a critical gap where most DSPM tools still fall short. Rather than requiring security leaders to lean on manual processes, Teleskope empowers them to define custom policies to remediate security issues and enforce controls at the source automatically. Security leaders can also choose whether they want to loop in a human for one-click approvals or allow Teleskope to enforce policies on their behalf. This is a capability we’re particularly proud of, as automated remediation flows are the only way for security leaders to enforce real-time data protection at scale.
Executing On That Vision: Teleskope’s Partnership with Ramp
Most data security solutions look strong on paper, but true validation comes from successful customer stories. Teleskope’s partnership with leading financial operations platform Ramp is what solidified that validation for our team.
Ramp had already invested in robust safeguards to protect its data footprint, but sought to implement even stricter standards, including redacting sensitive information across Slack messages in under three seconds. Existing batch processing tools were too slow, and their classification methods were unreliable. Ramp needed something better and faster to meet these new standards, which led its team to Teleskope.
The twist? At the time of the partnership’s inception, Teleskope wasn’t built for this capability, yet. However, we knew that tackling this challenge would both strengthen our solution while delivering on our vision to build what today’s security leaders truly need, so we didn’t hesitate.
Our team designed a new real-time pipeline, tailored for Slack and engineered for one goal: speed. We reimagined the process as a log flume: when a sensitive message appears, it doesn’t trickle through a sequence — it shoots straight to the end. This reimagined architecture enabled Teleskope to detect, isolate, and redact sensitive data in one uninterrupted flow. With the new system in place, Ramp achieved what it set out to do — and more. Teleskope now redacts sensitive messages in Slack in under two seconds, beating Ramp’s internal SLA of three seconds while dramatically reducing the risk window for data exposure.
Tackling this challenge alongside Ramp not only validated Teleskope’s approach to real-time data protection, but also confirmed the demand for proactive strategies that move at the speed of modern communication.
Enforce Real-Time Data Protection at Scale with Teleskope
Teleskope set out with a vision to build an end-to-end data security solution that seamlessly combines comprehensive visibility with automated remediation. Tackling complex technical challenges alongside innovative organizations like Ramp was what truly unlocked our platform’s potential.
Today, Teleskope continues to empower security leaders to discover and protect sensitive information across their entire data footprint in real time, not just after attacks occur. This proactive, automated approach empowers their teams to stay ahead of evolving threats and compliance demands with speed and precision.
Book a call to see how Teleskope can enable real-time data protection for your organization.
Introduction
Kyte unlocks the freedom to go places by delivering cars for any trip longer than a rideshare. As part of its goal to re-invent the car rental experience Kyte collects sensitive customer data, including driver’s licenses, delivery and return locations, and payments information. As Kyte continues to expand its customer base and implement new technologies to streamline operations, the challenge of ensuring data security becomes more intricate. Data is distributed across both internal cloud hosting as well as third party systems, making compliance with privacy regulations and data security paramount. Kyte initially attempted to address data labeling and customer data deletion manually, but this quickly became an untenable solution that could not scale with their business. Building such solutions in-house didn’t make sense either, as they would require constant updates to accommodate growing data volumes which would distract their engineers from their primary focus of transforming the rental car experience.
- list
- list
- list
- list
Continuous Data Discovery and Classification
In order to protect sensitive information, you first need to understand it, so one of Kyte’s primary objectives was to continuously discover and classify their data at scale. To meet this need, Teleskope deployed a single-tenant environment for Kyte, and integrated their third-party saas providers and multiple AWS accounts. Teleskope discovered and crawled Kyte’s entire data footprint, encompassing hundreds of terabytes in their AWS accounts, across a variety of data stores. Teleskope instantly classified Kyte’s entire data footprint, identifying over 100 distinct data entity types across hundreds of thousands of columns and objects. Beyond classifying data entity types, Teleskope also surfaced the data subjects associated with the entities, enabling Kyte to categorize customer, employee, surfer, and business metadata separately. This automated approach ensures that Kyte maintains an up-to-date data map detailing the personal and sensitive data throughout their environment, enabling them to maintain a structured and secure environment.
Securing Data Storage and Infrastructure
Another critical aspect of Kyte’s Teleskope deployment was ensuring the secure storage of data and maintaining proper infrastructure configuration, especially as engineers spun up new instances or made modifications to the underlying infrastructure. While crawling Kyte’s cloud environment, Teleskope conducted continuous analysis of their infrastructure configurations to ensure their data was secure and aligned with various privacy regulations and security frameworks, including CCPA and SOC2. Teleskope helped Kyte identify and fortify unencrypted data stores, correct overly permissive access, and clean up stale data stores that hadn’t been touched in a while. With Teleskope deployed, Kyte’s team will be alerted in real time if one of these issues surfaces again.
End-to-End Automation of Data Subject Rights Requests
Kyte was also focused on streamlining data subject rights (DSR) requests. Whereas their team previously performed this task manually and with workflows and forms, Kyte now uses Teleskope to automate data deletion and access requests across various data sources, including internal data stores like RDS, and their numerous third-party vendors such as Stripe, Rockerbox, Braze, and more. When a new DSR request is received, Teleskope seamlessly maps and identifies the user’s data across internal tables containing personal information, and triggers the necessary access or deletion query for that specific data store. Teleskope also ensures compliance by automatically enforcing the request with third-party vendors, either via API integration or email, in cases where third parties don’t expose an API endpoint.
Conclusion
With Teleskope, Kyte has been able to effectively mitigate risks and ensure compliance with evolving regulations as their data footprint expands. Teleskope reduced operational overhead related to security and compliance by 80%, by automating the manual processes and replacing outdated and ad-hoc scripts. Teleskope allows Kyte’s engineering team to focus on unlocking the freedom to go places through a tech-enabled car rental experience, and helps to build systems and software with a privacy-first mindset. These tangible outcomes allow Kyte to streamline their operations, enhance data security, and focus on building a great, secure product for their customers.


from our blog

